Disclaimer All information i write is of my own opinion, and is not reflective of AWS or Amazon.
Last year, i’ve been in a discussion with a customer about how to manage SSL certificates when you use an Application Load Balancer (ALB). Currently, as of January 07 2021, ALB’s have a maximum of 25 SSL certificates.
However, what happens if you want to host or support more than 25 certificates for your business? Let’s work through how we can resolve this.
The simplest solution to start with might be to use Rule-Based Routing on Application Load Balancers. This allows you utilise the same 443 port, but handle path or hostname based routing.
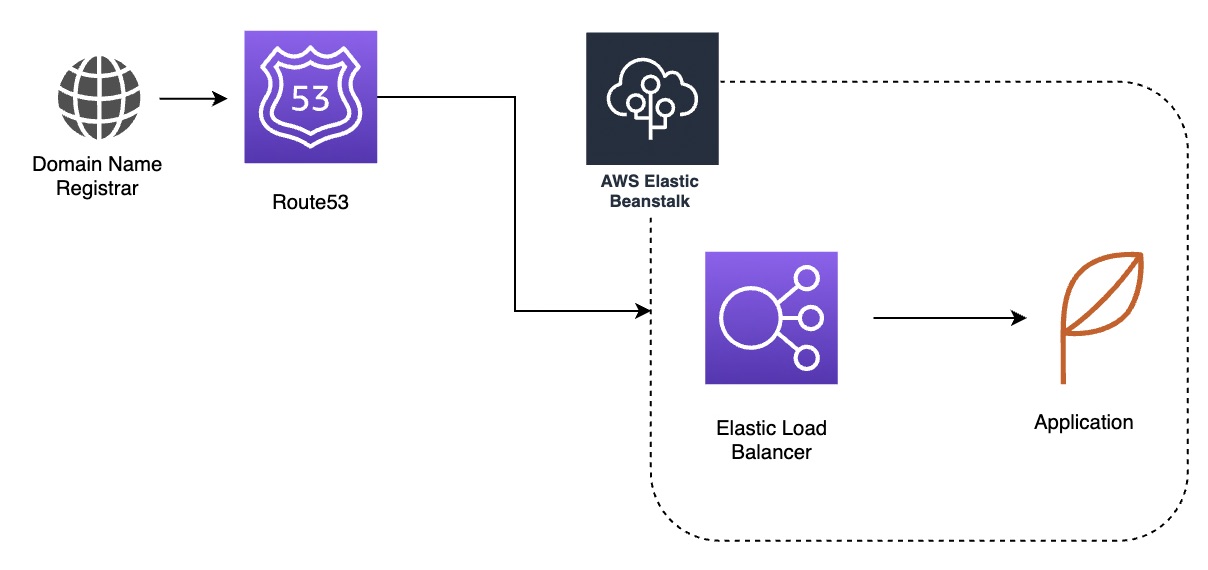
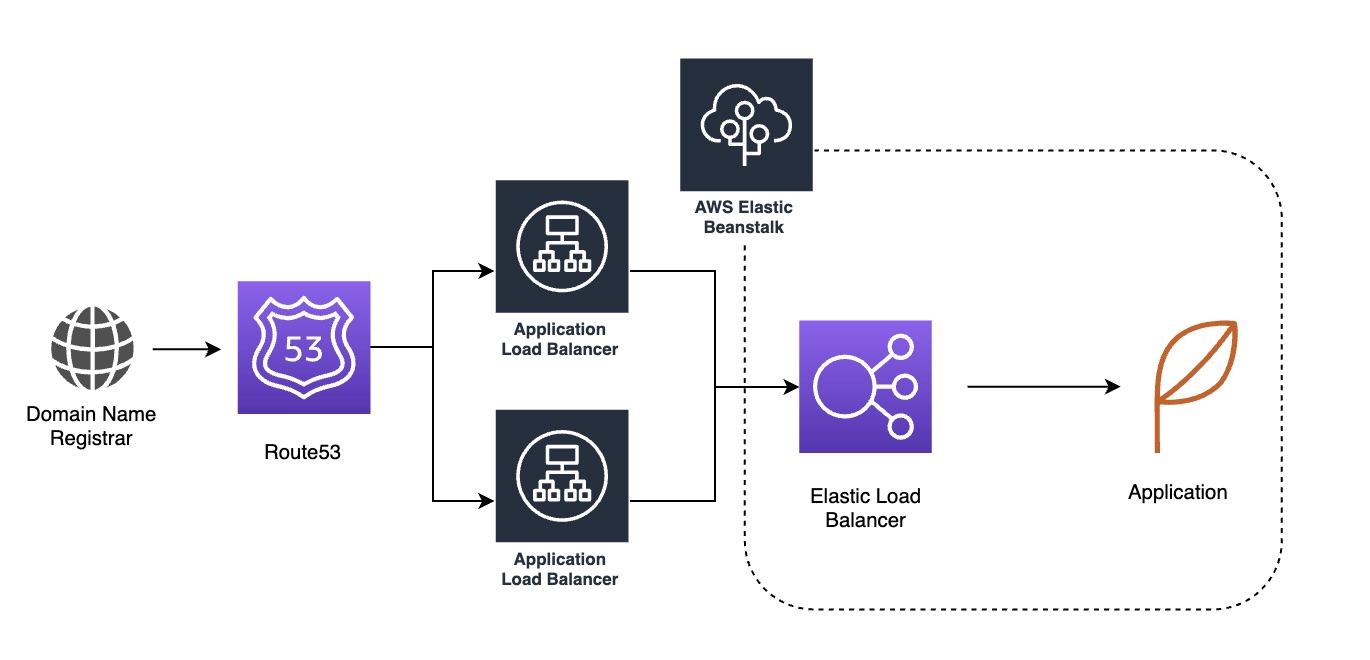
However, lets assume you have the following infrastructure and you are hosting a website for hundreds of customers.
The difficulties you are experiencing are that for each custom domain, you need an ACM mapping and also there is the 25 limit per ELB. You don’t want to keep creating ALBs just for a group of 25 certificates due to cost.
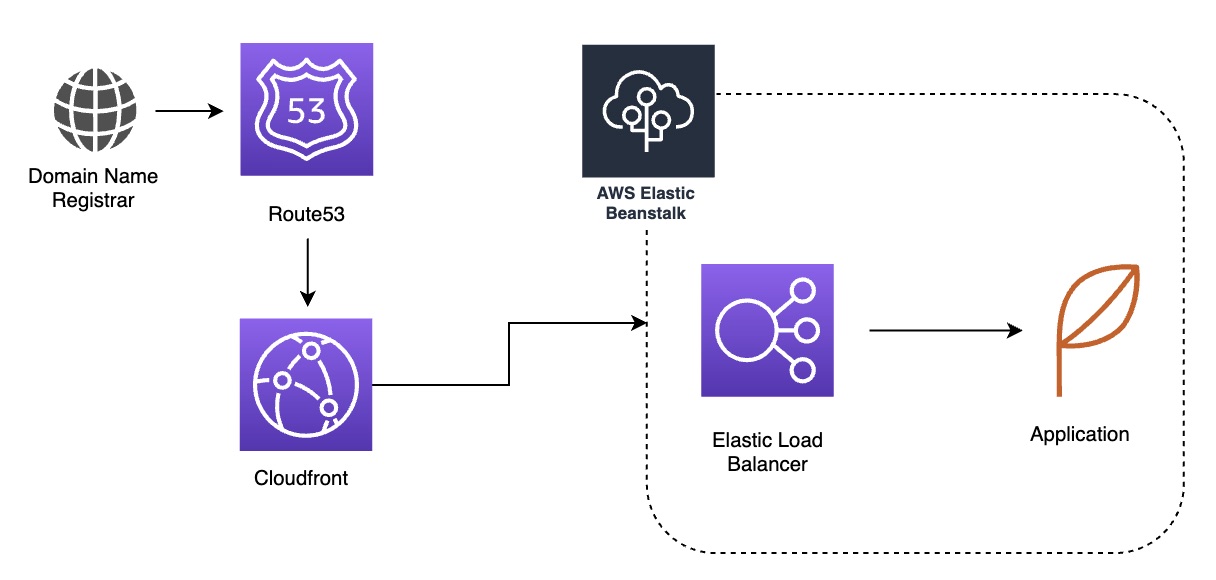
The First Method
The first method we can use is to implement CloudFront in-between Elastic beanstalk and Route53. This means that you can have as many CloudFront distributions that you would like to have, and assign HTTPS on CloudFront, setup ACM and remove the need for SSL to be done on the load balancer. However you can only associate a maximum of 1 SSL/TLS cert with each CloudFront Distribution.
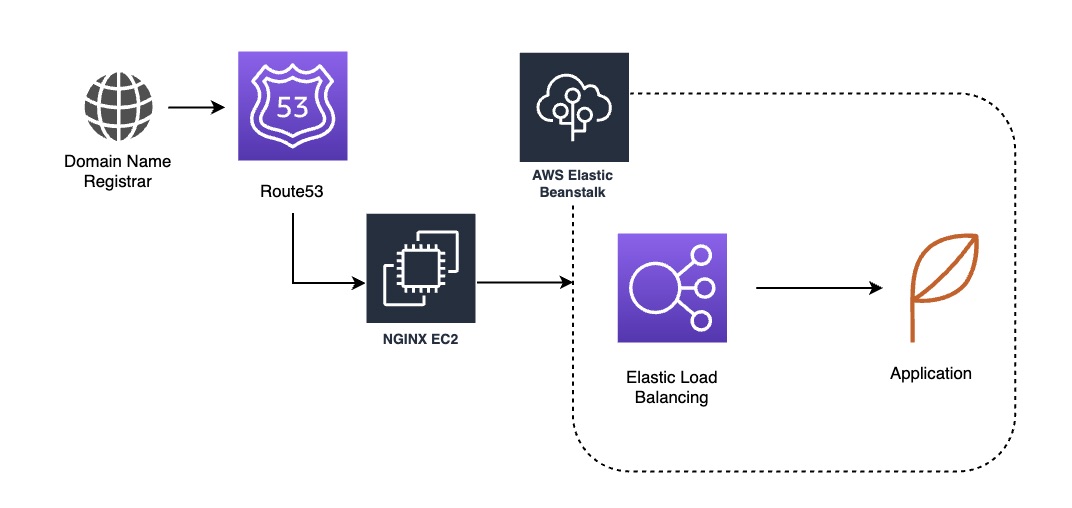
The Second Method
The second method is to implement your own proxy (HAproxy / NGINX). You do have to consider management overhead, plus you cannot take advantage of ACM to perform automated certificate rotation, as ACM only works in conjunction with select AWS services. You’d also want to script the certificate rotation process and have to manage scaling the instance. This is one of the most commonly used methods to work around the 25 cert limit at present.
The Third Method
The third method is more expensive, but you create multiple ELBs which then route to your elastic beanstalk. I’d be estimating the cost between this solution and the one above if you were going down the SSL proxy / gateway route. Looking to scale this you’d be adding n+1 LB, up to the maximum of 50 load balancers per region.
Personally in my opinion, it makes more sense to start with investigating whether the CloudFront route is a viable option, as you really want to remove the hassle of manually rotating certificates. You should remember to also setup an ALIAS record instead of CNAME (reduces the cost), and you could also encrypt the connection between CloudFront and your Elastic Beanstalk endpoint. The encryption is optional as it depends on your security standpoint and whether some websites needs internal encryption.
There is also a maximum of 200 CloudFront distributions per account, but this can be increased with a support request.
Any questions or concerns? Feel free to reach me at yiyang.tseng@gmail.com